Josep Ferrer on X: "Do you usually use SQL in your daily work? 𝘐𝘧 𝘺𝘰𝘶 𝘸𝘰𝘳𝘬 𝘸𝘪𝘵𝘩 𝘥𝘢𝘵𝘢, 𝘐 𝘣𝘦𝘵 𝘺𝘰𝘶 𝘥𝘰! Today, we're cracking the code on two SQL killer commands

Code for realizing virus killing function of MD5 special detection code... | Download Scientific Diagram

Password Cracking – What is a password hash? | University of South Wales: Cyber University of the year: Four years running: 2019, 2020, 2021, 2022

Carp Black Hash 3.5 kg Eimer, Killers Carp Bait Carp Fishing Carp, Carp Fishing, bait Boilies, Killers Baits, 24mm : Amazon.de: Sports & Outdoors
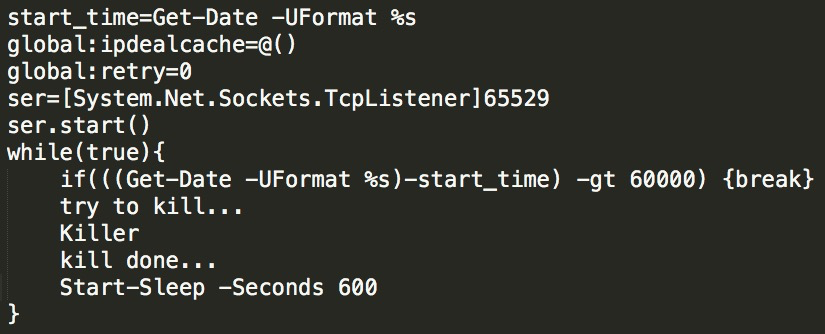
How Can We Defend against Multiple Intrusion Methods on Multiple Platforms When Lemon-Duck Is Continuously Active? - Alibaba Cloud Community
GitHub - usethisname1419/HashKiller: Decrypt Hashes. md5, sha-1, sha-256, shaw-512(unix), and Windows NT hashes. Multi-threaded and includes a saftey to prevent cpu exhaustion

Code for realizing virus killing function of MD5 special detection code... | Download Scientific Diagram